No items found.
Back to ShopProduct is not available in this quantity.

When the Model Context Protocol (MCP) was introduced, it was hailed as the missing puzzle piece for large language models (LLMs). For years, AI tools had been powerful in theory but hamstrung in practice, stuck inside text boxes, unable to act on the world. MCP promised to change that.
By standardizing how LLMs connect to external systems, MCP allows a model to plug into virtually anything: CRMs, SQL databases, document repositories, even cloud admin consoles. In a best-case scenario, it turns an AI from a chatty assistant into a full-stack operator, able to retrieve, update, and orchestrate across multiple systems in one conversation.
The vision was elegant. The reality is dangerous.
In simple terms, MCP acts as a “tool hub.” It sits between your AI model and the services you want it to access. Each “tool” is a small connector, a script or API integration that tells the AI, “Here’s how you talk to this service, and here’s what you can do with it.”
But this convenience comes with three serious problems:
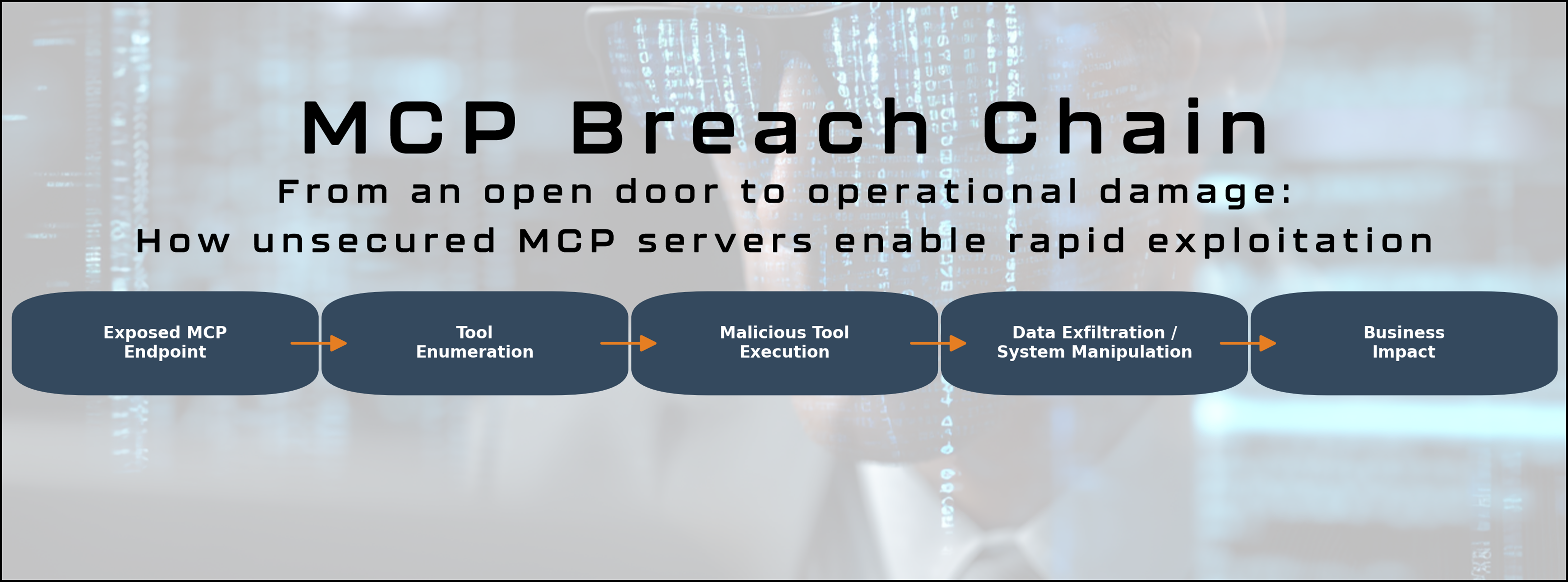
If that sounds like a privileged API gateway with no locks, no alarms, and no front door… that’s because in most cases, it is.
Security researchers have already found over 1,800 publicly exposed MCP endpoints in live production environments. In many cases, these servers were:
And these aren’t just small personal projects. Some belonged to well-funded enterprises with regulatory obligations. Others were connected directly to SaaS platforms containing personally identifiable information (PII) and financial data.
The scale and sensitivity make MCP exposure a ticking time bomb.
The following cases, a mix of public incidents, anonymized breach reports, and red-team findings, illustrate the attack patterns and business impacts MCP creates.
In August 2025, a vulnerability dubbed CVE-2025-54136, nicknamed “MCPoison,” made headlines in AI developer circles. The flaw targeted how the popular AI coding assistant Cursor managed its MCP configuration files.
The playbook was simple but devastating:
The new code gave attackers persistent remote code execution inside the developer’s environment, with access to linked GitHub repos, cloud storage buckets, and API keys.
What made MCPoison particularly dangerous was its stealth: no alerts, no prompts, and no visible indication that anything had changed.
This corporate breach began not with an exploit, but with a gift.
An engineering team received an email from a known industry peer sharing a “fantastic new summarizer tool” for MCP, designed to condense large project documentation for faster review. It worked flawlessly.
Except for one hidden feature. Every time it processed a document, it also sent a copy to a remote server controlled by the attackers.
By the time the breach was discovered, three months of internal project plans, product roadmaps, and client proposals had been siphoned off. The company never determined whether the leak reached competitors, but suspicious bidding patterns in subsequent contracts suggested the worst.
In a red-team exercise for a mid-sized SaaS company, testers discovered an MCP endpoint exposed to the internet with no authentication. The tools connected to it included:
The testers didn’t need malware, phishing, or privilege escalation. They simply sent a tools/list request to the open endpoint, found the commands, and issued API calls, successfully altering invoice records and creating false refunds.
Had this been a real attacker, the company would have faced both direct financial loss and regulatory exposure under payment card and fraud prevention laws.
The Practical Cybersecurity Decisions framework starts from the business end, not the tech end. With MCP, the stakes aren’t just about “losing some data.” The impacts can cascade:
For many organizations, MCP sits at the intersection of trust, revenue, and operational continuity, meaning a single lapse can affect all three at once.
Across public reports, incident responses, and controlled testing, five main threat patterns keep surfacing:
The obvious reaction is to “lock everything down”, but MCP’s business appeal is speed and flexibility. Security that strangles usability won’t survive adoption.
Instead, the goal is strategic containment:
Even partial implementation of these steps can raise the cost and complexity of an attack dramatically.
MCP is still early in its adoption curve, but the trajectory is clear. It’s being embedded into developer environments, customer service platforms, and back-office automation at a pace that outstrips security awareness.
This is exactly the phase in technology adoption when avoidable mass-breach patterns tend to emerge, the “open S3 bucket” era for AI integration. Organizations that act now will avoid becoming tomorrow’s cautionary headline.
At our core, we focus on building capable, adaptable cybersecurity specialists who can think critically about evolving threats, not just follow checklists. Our training emphasizes the ability to assess real-world systems, identify where the highest-value risks lie, and apply security principles in a way that supports, rather than hinders, business goals.
By equipping professionals with both technical depth and strategic perspective, we ensure they can respond to incidents decisively, anticipate emerging risks like those in MCP, and integrate security as a natural part of everyday operations.
→ Explore our hands-on, business-aligned cybersecurity training programs.
Daniel Wilson
Cyber Intel Training
Practical training for a safer, smarter, more cyber-aware society.